Today a simple update from my Cyber Threats Observatory (available HERE). Six months of this crazy year are over and it’s time to check some cyber threats trends. Once upon a time there was Emotet. It was on the TOP 5 on every ranking list, it reached the 5th epoch and it was able to deliver many implants and direct Malware. Nowadays we see AgentTesla as the main threat over the web. Increasing from 6 months ago SmokeLoader and Zegost. Trickbot noticeably decreased its magnitude (since its takedown, its resurrection and its second takedown) while MyDoom persists over time even if with small amount of activity.

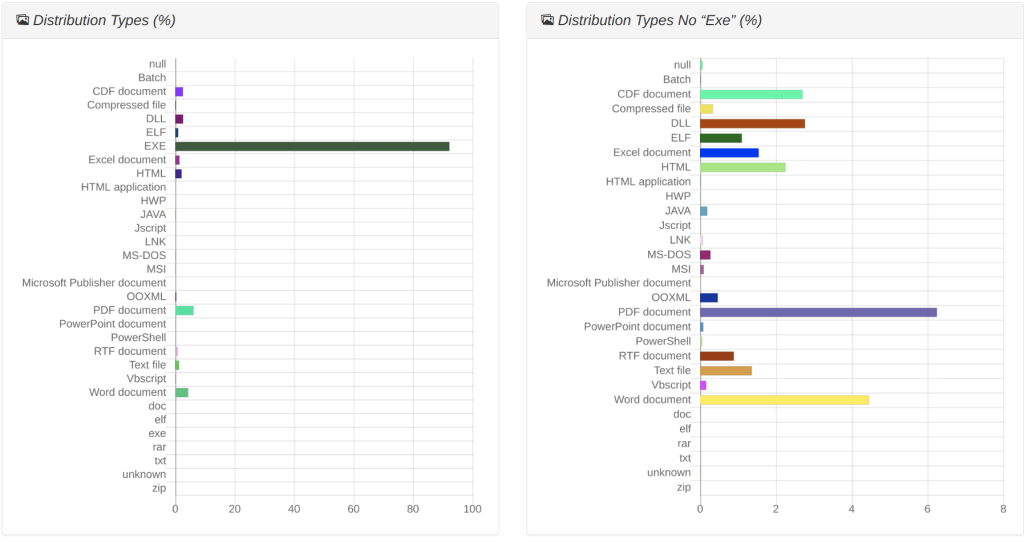
On the other hand the file distribution looks like quite similar over the time. If we consider the portable execution by def, with .exe extension (on the left side of the following image) we see they still take the vast majority of samples. Indeed samples over Microsoft office et. Al. still drop and execute many .exe malicious files. If we exclude the .exe extension (on the right of the following image) we might better appreciate the original droppers. PDF and Microsoft Word documents (.docx,.doc,.dotm, .rtf) are in the first infection stage, while .html, .cdf and .dll overtook the Microsoft excel extensions which were one of the most important malware carrier in 2021.

Now let’s move to the stereotype quick analyses. In particular domains, files and processes name stereotypes are constantly tracked to spot time deviations. First of all I’d like to focus on AgentTesla, since one of the most active cyber threat in the current panorama. The following image shows the different stereotypes. On the left we have “file names”. It looks like AgentTesla saves many local files as images (png, jpg, and so on) and, according with my machine learning algorithm, a name called asyncclient.exe looks like to be the best centroid to be looked for during analysis. On the other side of the image, processes name stereotypes are showed. Nice to see many known processes used in multiple infection chains have been discovered. Many of them are most significant for AgentTesla such as regasm.exe, reg.exe, prevhost.exe, while others are general purpose ones such as ping.exe, arp.exe, cmd.exe and so on and so forth. On the center of the following image the domain names stereotypes. Interesting the google-a.com and milla.publicvm.com have been chosen as most relevant domain name the agenttesla communicate with.



Conclusion
If you want more graphs and statistics, you definitely want to daily check this page.
Cyber Threats are evolving over time and I believe it’s important to track them and to study their own evolution in order to be able to recognize and to block them as quickest as possible. If you also believe in tracking activity and you want to help my work, please consider to contribute by donate few bucks on the Cyber Threat Trends project page (HERE).